Phishing attacks
If a user receives a suspicious email, they can check the home page at https://portal.upol.cz - there is often a warning about spam, including questionable text. We also share the warning on the networks Facebook and X. The user can also contact their network administrator. It is definitely necessary to check the sender's address and not click on any links in the text. General information on cybersecurity can be found in the article on UPWiki.
Phishing
This is a type of attack that uses email communication to obtain sensitive user data. Its name is a corruption of the English word "fishing". The attacker throws bait to his victim and waits to see if the victim takes the bait. The most common types of phishing messages are a call to update security data, a problem with the user account, email box, information about a failed payment, bank account or customer satisfaction survey. Attackers most typically target emotions such as fear, trust, authority. The messages usually require a username and password or encourage you to log in to a fake website.
Phishing emails are usually sent from an address that does not match the sender's name. The email message usually has poor grammar. The links contained in the email have a suspicious domain (e.g. upol.bz instead of upol.cz, rnicrosoft.com instead of microsoft.com [RN instead of M]). The message encourages you to enter sensitive data, trying to scare the recipient into an immediate reaction. The email message always puts pressure on the recipient to take some action quickly, otherwise he will be threatened with account restrictions, etc.
What to do if you come across a phishing email?
If the user has already clicked on a suspicious link, they need to change their password and verify their account settings as follows:
- First change your password (log in to https://portal.upol.cz - top right icon 3 horizontal lines - link Change password).
- Then log in to your email via the web interface https://outlook.com/upol.cz and look at your email settings.
- Click on the gear icon at the top right and go through settings Rule, or Forwarding and cancel settings that do not belong there.
- Please check your settings, ideally on a classic PC or tablet, not on a mobile phone. Unfortunately, not everything is displayed there.
- Once you have done this, send a test email to an external address and from the external to your university address.
- If the emails are delivered correctly, your email is fully functional.
- If the account has been compromised, MS Office will block the user's outgoing mail and report an error message when sending:
Your message is being blocked by a custom mail flow rule created by an administrator at upolomouc.onmicrosoft.com. Blocked by administrator due to account attack. Change your password and contact CVT UP.
- In this case, the mail administrator must unblock the account manually - write a request to Helpdesk in the category Network services (employees) or IT and networks (students), enter your nationality, confirm that the password has been changed and the account has been checked, and the account will then be unblocked by the administrator.
Check the address bar
You can often access fake dangerous websites by clicking on a link in a fake email. If you want to go to the site, it is worth opening a new browser window and rewriting the web address yourself. Even a small change in the web address can indicate whether it is a fake website. A dot may be replaced by a dash, or a single letter may be replaced by a similar one. Always check the address bar. You can check that you are on the correct page in your browser by clicking on the green lock icon.
Examples of phishing attacks at UP
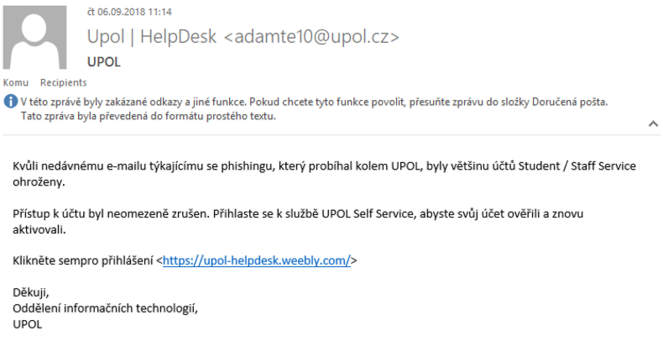
This phishing email uses a real link to UPWiki. However, upon closer examination of the link, it is clear that the clickable link has the domain upol.bz, not upol.cz. Moreover, the visible text is not always identical to the link. In case you open the link, always make sure in the browser address bar that you are really on the right page or use the tooltip.
#2
This e-mail has a ton of typos, but as it is in Czech, foreign users might get confused. There is no Information technology department at Computer center.
#3
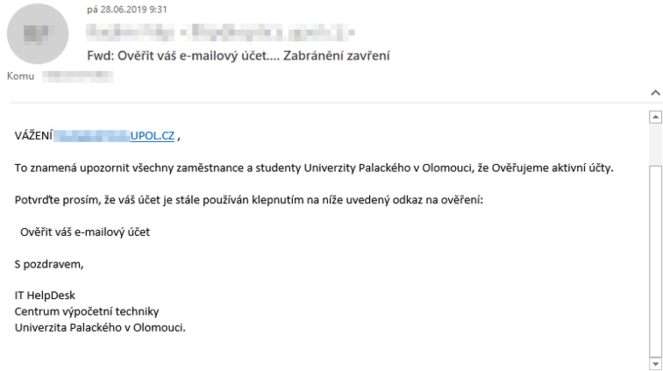
This phishing attack tries to convince you that CVT will deactivate your account unless you click on a link (which is not there). We will never inform you by email that we are verifying active accounts. User accounts at UP have a preset validity period - the account is deactivated 60 days after graduation or employment. After 180 days, the account is deleted.
#4
As with the previous phishing email, the attacker tries to force you to click on a link. The email is suspicious in both its subject and sender.
#5
Similar to the previous email, there is poor Czech and grammar here. The attacker is trying to push for quick action via a link = proven manipulation so that the person does not search and does not think much before clicking. The email and the link do not come from our domain upol.cz.
#6
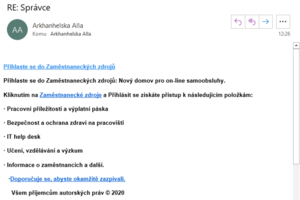
This is a typical phishing disguised as a corporate message. It looks like a response from someone outside UP who sends a link to some "Employee Resources". The text tries to act like an internal notice from the HR department. The "copyright © 2020" does not make any sense as well as the Czech grammar is terrible.
#7
First of all, you need to notice the nonsensical text about the "2024–2025 directory". The directory is not updated by year like a school list. It is a pure fabrication to make it sound important. Again, there is pressure and threats of losing access to the account. The aktualizace/ověření ("update/verify") link is also suspicious. Then there is bad Czech, incorrect use of upper and lower case letters.
#8
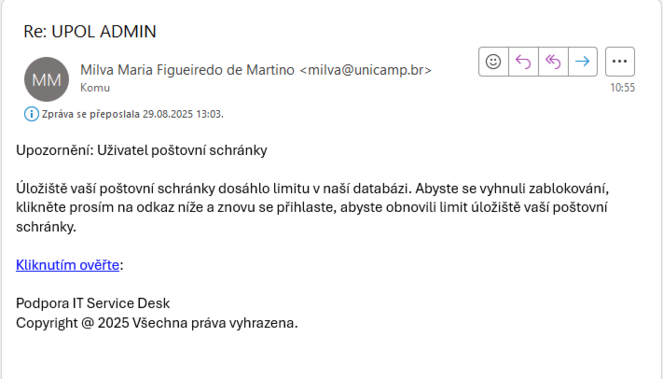
This email pretends to be a notification that your mailbox limit has been exceeded. The message is fake simply because it comes from a foreign email domain (unicamp.br), does not properly identify the university as the sender, and invites you to log in via an unverified link that is incorrectly formatted as "Kliknutím ověřte" ("Click to verify:"). This communication uses coercive language with the threat of account blocking, which is a common way to obtain access data.
#9
This is a phishing email that pretends to be an official message from the university IT administration. The attacker uses an urgent tone and a fake link to obtain the user's login details. The email contains inauthentic elements such as incomplete contact information and general wording, which indicates its fraudulent nature. The text „Aktualizovat zde (S)“ ("Update here (S)") leads to a fake page where the attacker obtains the login details.
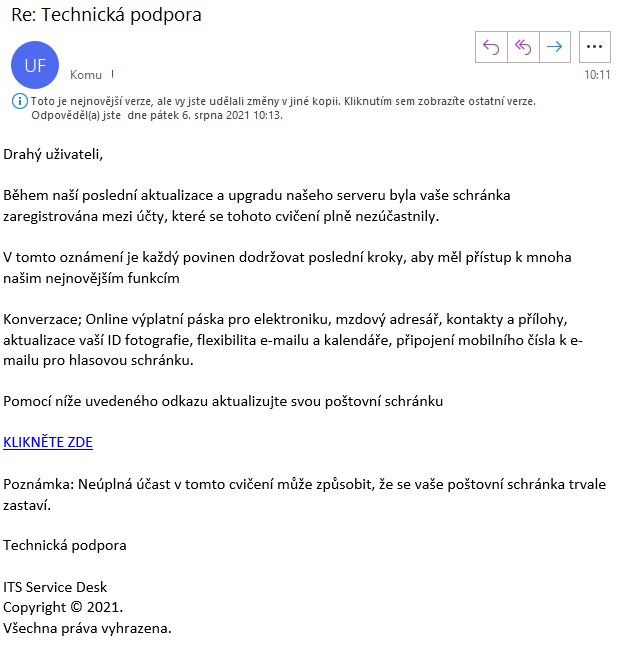
#10
The email pretends to be a technical support message and reports an alleged problem with mailbox registration after a server update. The attacker uses an urgent tone and the threat of losing access to features to trick the user into clicking on a „KLIKNĚTE ZDE“ (“CLICK HERE”) link and performing an unauthorized action. The content of the message contains unclear wording, missing official contact information, and a generic ending, suggesting a fraudulent nature. There is also poor grammar, unusual wording, etc.